Construction Industry Webinar: From Code to Compliance – Mastering the Building Safety Act 2022
Join us for our upcoming live webinar – “From Code to Compliance: Mastering the Building Safety Act 2022” 🗓️ Date:
Read articleEvents in the last few weeks indicate that criminals are developing what can only be described as powerful weapons in the form of new botnets utilised in novel ways. The use of these botnets is underpinned by organised, structured business models (such as Ransomware as a Service) and payment mechanisms. To give these some context, I thought it first useful to dip into the history of mainstream digital ransoms and the evolution:
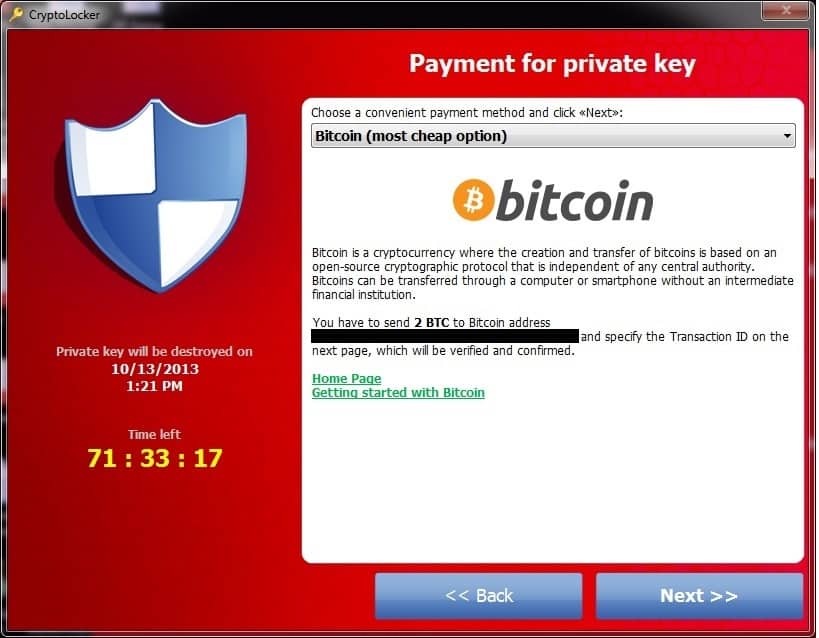
In 2013, one of my engineers showed me a laptop he’d brought back to the lab for a customer whose files had all been replaced with oddly named files he couldn’t open and a ransom message was on the screen. This was my first view of CryptoLocker, very much step change for ransomware that made them all the more attractive to criminals, it also took advantage of a decentralised payment mechanism: Bitcoin.
Alongside encryption of files, some criminal groups took a simpler approach, flashing up inappropriate images, nuisance messages or interference – in some cases disguising the activity as a legitimate license renewal such as claiming a copy of Windows had expired and mimicking the Windows Activation Wizard.
One of the simplest methods of protecting against an encryption ransom attack is to ensure you have ring-fenced backups of your data however, faster connections and novel exfiltration techniques have meant that before files are encrypted, they are copied to a remote location operated by the attacker. If you refuse to pay the ransom, the files on your servers will remain encrypted but don’t worry, you’ll be able to download them all from the Internet where the attackers have helpfully published a copy for all to see!
Earlier this month (9th September 2021), DDOS (Distributed Denial Of Service) mitigation company Qrator Labs published an article about a massive DDOS attack it had monitored from a large botnet that was attacking at the application layer (making legitimate requests to the web application) as opposed to lower-level attacks such as SYN flood attacks. An application layer attack is much harder to mitigate with infrastructure because the requests are indistinguishable from a legitimate request until they reach the application server. Once you know a request isn’t legitimate, all you can do is block requests from that “user’s” IP address but now you have a new problem: how do you maintain a block list of tens-of-thousands of IP addresses that you can lookup in real-time with reasonable performance?
The attack observed by QRator was huge but short lived, leading many to believe it was a test-fire. Unfortunately, this means that there is a botnet ‘out there’ capable of launching huge attacks against targets that is very difficult to mitigate.
The reason I mention Mēris and the development of novel botnets: attackers are now taking commercial services offline with DDOS attacks and demanding a ransom for restoration of the service. Targets are being carefully chosen and just this month (September 2021) there was a campaign of attacks against VOIP providers who have limited options for mitigating application level attacks against their services.
What does this mean?
Ransomware is growing but even if it were a thing of the past, new methods/vectors for are appearing all the time, as evidence by the VOIP DDOS attacks and organised development of new botnets like Mēris.
While most organisations aren’t likely to be targeted directly, services they rely heavily upon could be. Banking, accounting solutions, IP telephony, web-based portals/interfaces, APIs, etc. could be impacted.
There are some attacks you simply cannot prevent but this doesn’t mean you can’t prepare, even if just at a business continuity plan level.
Does your business continuity plan include a provision for your telephony provider being offline at short notice and for a prolonged period? Will you simply deploy mobile devices? If so, who will communicate the numbers, where will you get them from, how will you update customers, suppliers and staff? If your payroll SaaS solution is taken down at the end of the month, what processes do you have in place for a manual payment run?
Ultimately, services & products are only ever part of the solution and without management of them and careful consideration of your assets, risks, threats and mitigations; attacks will always have the potential for significant impact.
A risk-based approach maximises your security posture while making ensuring budget is spent in the most effective way. If you like assistance in tackling you information security, are interested in practical improvements and/or would like to have your certification to a standard (such as ISO 27001 or Cyber Essentials), get in touch!
We understand there are many options to choose from and you want to make sure the tool you adopt is the right one for you.
"*" indicates required fields
Construction in Crisis! Written by Chrissie McAnelly, Cybit Data & Analytics Consultant – Construction Sector The construction sector is
Read articleBy Asiel Esgair – Cybit Data & Analytics Consultant – Public Sector & Local Authority In our
Read article